MONITOR OPERATIONAL TECHNOLOGY AND REMOTE CONTROL SYSTEMS
IMPLEMENT INTRUSION
AND THREAT DETECTION
SECURE DISTRIBUTED
ENERGY RESOURCES
CYBERSECURITY IN DISTRIBUTED ENERGY RESOURCES
Detecting Attacks and Establishing OT Visibility
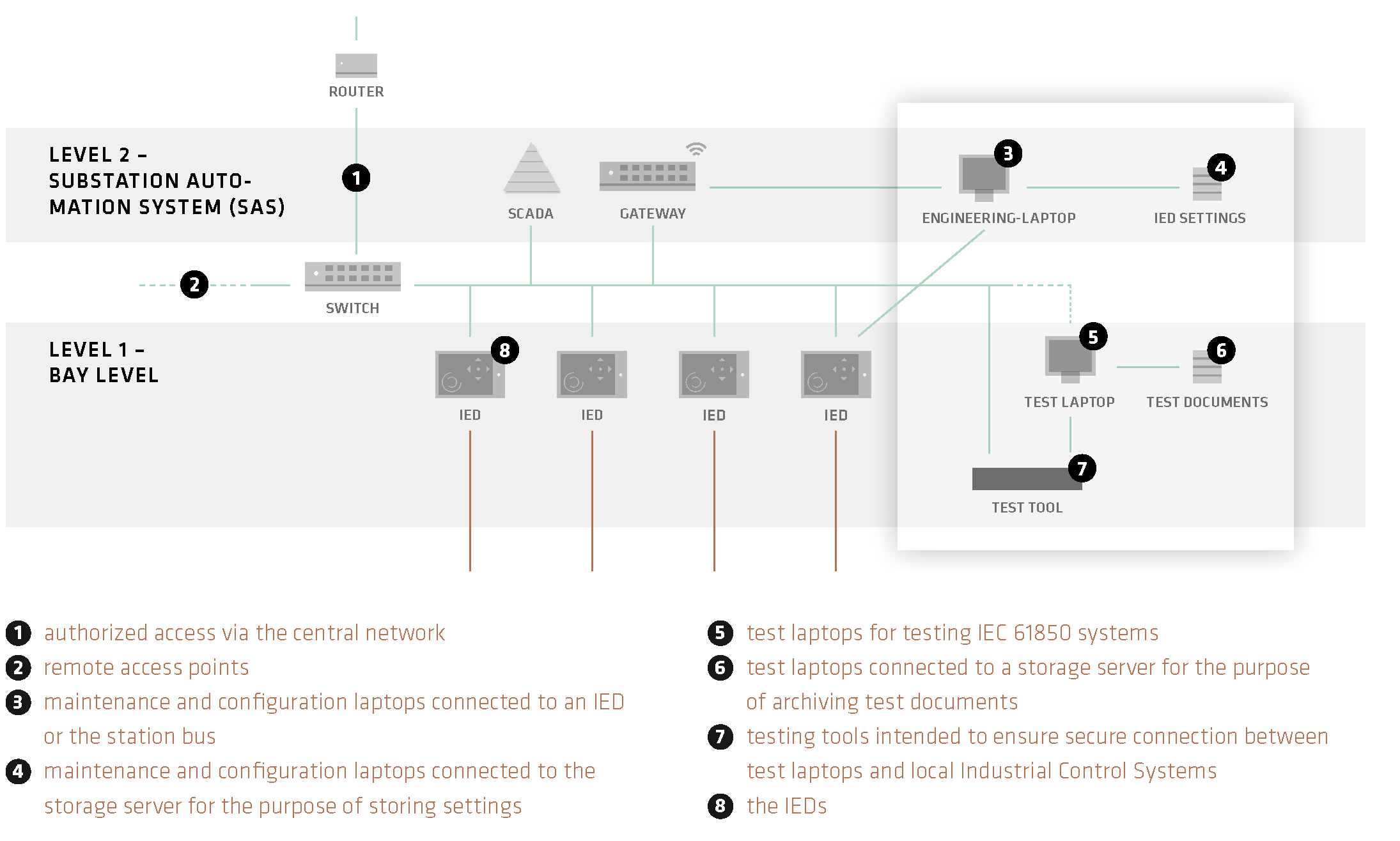
Energy supply systems are becoming increasingly efficient and resilient thanks to system integration (sector coupling), internationalization, distributed energy resources, and digitalization. This cross-sector and, in many cases, cross-border system integration requires smooth, unimpeded data exchange between all actors involved, i.e. between power plants and transmission and distribution system operators, local public utility companies and prosumers. The IEC 61850 standard defines the basis for interoperability of the industrial control systems used.
Yet, this connectivity also heightens the risk exposure of these networked infrastructures to cyber threats. One particular challenge for energy suppliers lies in implementing and managing cybersecurity across distributed, interconnected installations at multiple locations. This is hampered by the fact that switchgear systems, transformer substation and distributed energy resources are only rarely staffed with people specifically tasked with cybersecurity and error mitigation of Industrial Control Systems. Many such locations are entirely unmanned and remotely operated. Effective security solutions must therefore be holistic, interoperable, and lean.
KLAUS MOCHALSKI @ IEC 61850 WEEK 2021
Gaining Risk Awareness
The IEC 61850 standard itself does not define any specifications for the data and system security of the central and local OT. Related standards such as IEC 62351-4 and IEC 62351-6 recommend security measures, but these can only be implemented to a limited extent in real operations. In addition, there is a multitude of access options for adversaries that neither firewalls nor classic intrusion detection systems (IDS) can detect.
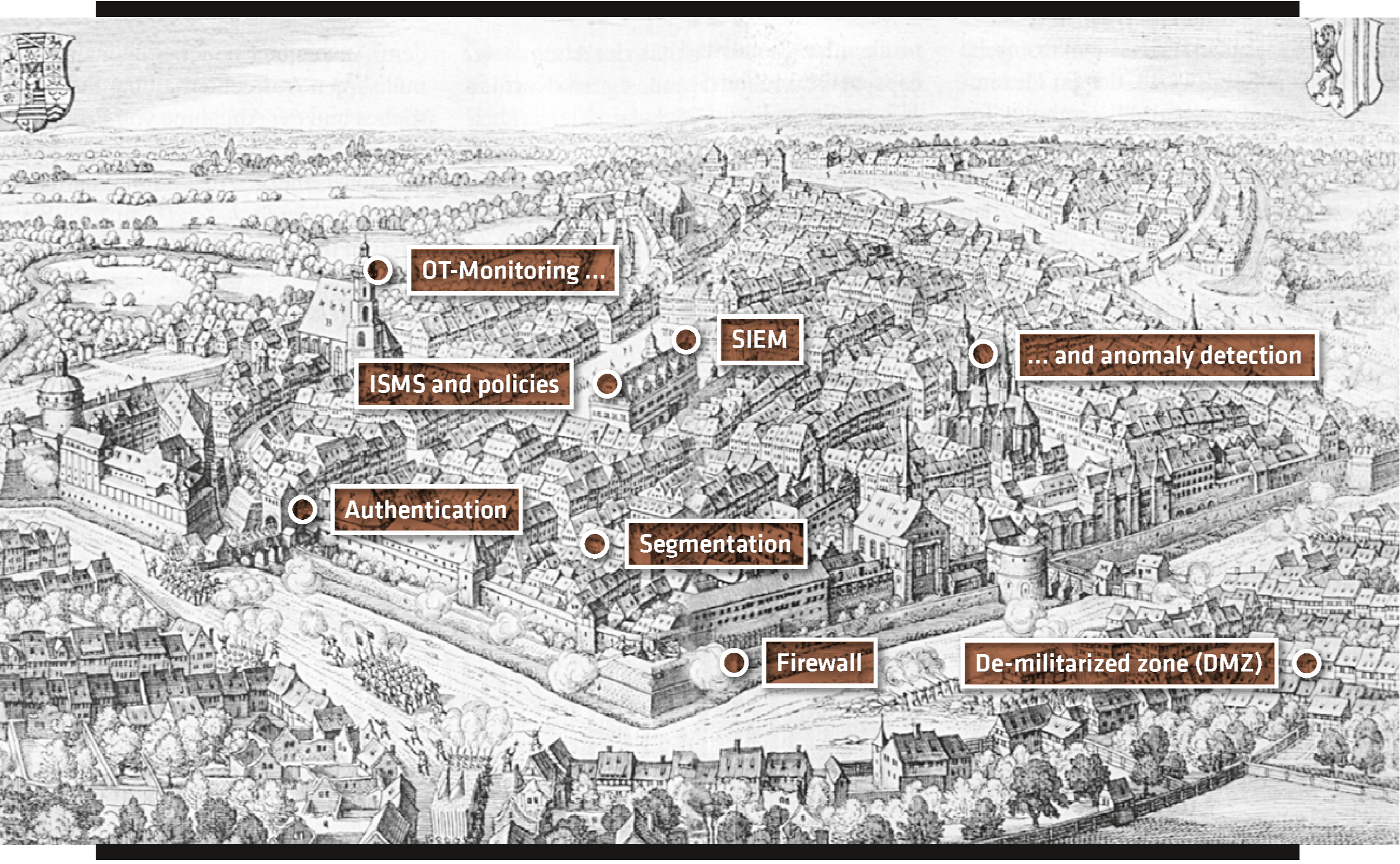
Establishing Defense-In-Depth
A state-of-the-art, strongly connected network must be secured like a modern city state (to simplify the picture). The city walls, gatekeepers and the military (i.e. firewalls, data diodes and authentification) secure the city against visible, known external threats. The inhabitants follow the mandatory standards and legislation (ISMS, IT and compliance guidelines). The police and the organs of the Federal Office for the Protection of the Constituition are responsible for domestic, i.e. internal security within the country or city. Currently, most energy suppliers only secure the borders of their OT and ICS. Few industrial networks have mechanisms in place for ensuring internal / homeland security.
WHITEPAPER ON IEC 61850 STANDARD

Next Generation Intrusion Detection in Energy Resources
The whitepaper »360° Cybersecurity in IEC 61850 Infrastructures« addresses the security requirements and solutions for modern electrical supply systems. It focuses on the visibility and security of industrial networks (OT, ICS) in distributed energy resources such as substations, switchgear, and renewable energy resources.
You learn:
- which advantages the IEC 61850 standard offers for planning and operational management;
- which risks and specific attack vectors IEC 61850 infrastructures are exposed to;
- why classic security mechanisms are not effective;
- how to implement a Defense-in-Depth concept that meets the requirements national IT regulation and standards;
- how a Next Generation Intrusion Detection System for OT can take advantage of the IEC-61850 standard, make risks visible, and help prevent cyber attacks, manipulation, and operational disruptions.

Rhebo's solution has been very well established with German utilities for years. And as a German and vendor-independent company, it offers the trustworthiness and flexibility that our customers expect when securing their system-relevant infrastructure.

With Rhebo, we can not only thoroughly test and prove that our network control technology is running securely and stably, Rhebo also provides us with detailed insight into our telecontrol technology and process network control in order to quickly detect, limit and rectify new types of attacks and misconfigurations that would otherwise be difficult to see.

With Rhebo, we can be sure that any anomaly in our network control technology is reported in real time and that we can react immediately.

We were impressed by the smooth process and the direct development of sensible measures prepared us very well for upcoming cyber security risks.

The newfound visibility and analytics capability with Rhebo has allowed us to visibly improve the performance of our SCADA technology and the cybersecurity of the wind and PV farms we operate.

Rhebo Industrial Protector impressed us with its functionality, depth of detail and real-time detection of even hidden anomalies.
GET WHITEPAPER NOW
FIND OUT HOW TO SECURE YOUR DISTRIBUTED ENERGY RESOURCES WITH RHEBO
Get in touch to schedule a web demo

